
Today we will talk about identity theft, since within the global world of electronic commerce there is a diversity of means to advertise such as social networks, a powerful influence on current decisions to buy and sell products and services.
Many times within these networks, there are people who pretend to be another, to obtain a product or service on behalf of a holder who has no idea what is going on, so identity theft is a current issue that needs to be addressed.
Spoofing
A current problem and crime in most cases is identity theft, either in your email, with services or products purchased online or on your social networks. To solve this, it is recommended that you read this article to the end, here are the main ones spoofing cases and how to prevent them.
Impersonation is basically posing as someone else on the Internet to perform illegal acts.
What do they impersonate for?

Although the reasons vary in most cases, the most common case is to annoy or know something about the person impersonated. This is also done Illegal act creating profiles to commit sales fraud on behalf of third parties.
The most common place where these impersonations take place is in the main social networks since I get all the personal information of a user specific is very easy and at hand, as well as create a fake profile with stolen photos to impersonate the person.
Regarding the profile of the people who are normally victims of an impersonation, They are commonly people who have your personal information such as name and surname, date and place of birth, photographs, etc. In a public social network, that is, do not control who can access this data. It is very common for people to think that this only happens to public people such as athletes or artists, which is false, anyone can be a victim of fraud.
What ways are there to impersonate a person?
- Illegally accessing the account. In this way, the offender must obtain the access code corresponding to the victim, either by guessing it, by means of a Phishing, or some kind of malware to obtain it.
- Creating a new and fake profile, with the total or partial information of the impersonated victim. It is much simpler than the first, where the criminal only has to choose the victim, collect their information and create the profile.
Creating a false profile to supplant the identity of any person is a crime that violates the right to one's image as mentioned in article 18 of the Spanish Constitution, in addition to the fact that article 401 of the penal code establishes that you can go to prison for this illicit.
Access another user's account. This fact is reportable since it attacks the privacy of the victim, and the offender receives two charges, for illegally entering the account and for improperly obtaining the password.
What ways are there to impersonate a person?

- Illegally accessing the account. In this way, the offender must obtain the access code corresponding to the victim, either by guessing it, by means of a Phishing, or some kind of malware to obtain it.
- Creating a new and false profile, with the total or partial information of the impersonated victim. It is much simpler than the first, where the criminal only has to choose the victim, collect their information and create the profile.
Creating a false profile to impersonate anyone is a crime that violates the right to one's own image as mentioned in article 18 of the Spanish Constitution, in addition to the fact that article 401 of the penal code establishes that you can go to prison for this offense.
Access another user's account. This fact is reportable since it attacks the privacy of the victim, and the offender receives two charges, for illegally entering the account and for improperly obtaining the password.
How to reduce the risk of information being stolen?
To significantly reduce the risk of being spoofed online, here are some tips.

- Using complicated passwords to access the profile of the social network. You do not need a long password, but one thing that works to increase the difficulty of finding it is to put uppercase and lowercase letters and a number.
- Know what phishing is. This is a common practice that consists of sending victims, emails or messages by other means, who request to validate the profile of the social network in which they want to obtain your password, under any excuse, in order for you to enter this link to confirm your account and thus, the offender will obtain your information and password.
- Make your personal profile as private as possible, thus preventing unknown users, completely outside your social circles, from accessing your personal information. Something to consider is when you accept friends, first of all, check the people they know in common, as well as try to find out why I add you or for what purpose if they do not know each other personally.
- Do not share personal photos or videos. Criminals seek these contents and then extort money from the victims under the premise that if they do not meet the requirements established, they will make this information public.
- Review the terms of service and privacy policies of the pages to which we give them access from our account, to know what they share of your data, how they will treat them and if they are shared with third parties, etc.
If the usurpation behavior consisted of the name only, without photos or other information, it may be a namesake and you cannot take any legal action.
For If the profile does use our photograph or our data, an illegal act would be taking place.
This behavior is punishable by article 401 of the Penal Code, as a crime of identity theft, with a prison sentence of six months to three years.
What to do when faced with identity theft?
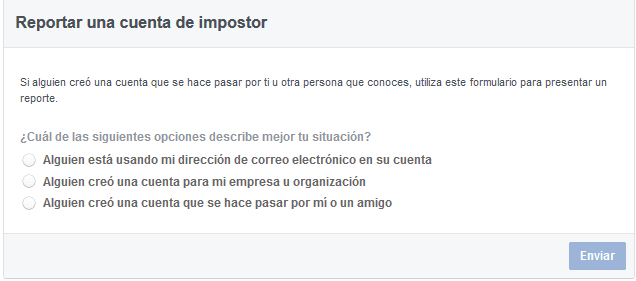
First of all, you must identify the fake profile, in the social network in which it is, an example Facebook allows you to report for these reasons, so it is essential so that it does not continue to use your information.
You can file your complaint with the State Security Forces and Bodies (FCSE). You need to provide evidence of how you are being victim of identity theft. To have proof of this, save some screenshot of the fake profile, as well as the information that belongs to you and is being misused.
Spoofing It can happen to anyone, it does not matter if they have profiles on social networks or not. For this reason, we must periodically search for our full name to know what is published on the Internet about us and why.
25% of Spaniards who have accounts on social networks, claim to have been a victim of this crime at some time.
However, you don't have to be famous to be targeted by phishing. For example, the case of a young woman who had her identity stolen to create a profile on a dating site and date other men on her behalf. There are also cases of impersonation before credit institutions, card cloning and even in the civil registry.
- File your complaint with an official institution: The moment we know of the illegal act, you should go to an institution to anticipate the probable consequences.
- Claim payment of the debt: If, as a consequence of identity theft, you are being required to pay an unrealized amount, you can claim before the Consumer Arbitration Boards. You can also make a complaint to the Telecommunications User Service Office.
- Go to the person who generated the debt to cancel it: In the event that the victim knows that their data has been included in a delinquency file for refusing to pay for a product or service that they did not purchase, they must go to the company or person that charges them demanding the cancellation of their debt, as well as to be removed from the mentioned list, providing you with a copy of the impersonation evidence.
- The documentation: If the citizen decides to report identity theft, it is necessary to carry all the documentation that indicates the product or service whose contracting is being attributed, indicating the associated account number and adding a written copy of the claim that has been sent to the company. It is extremely important to provide a copy of the invoice for the product or service involved in the event.
In conclusion:
Identity theft is a serious social problem, which actively attacks all people, without distinction of race, ethnicity or creed, the Internet, by becoming such an open network, also allows the entry of people with malicious will, so we must constantly be protecting our information, and above all to know well who we are giving it to, because nowadays few websites are reliable.